Introduction
Command and Control (C2) Frameworks are an essential part of both Red Teamers and Advanced Adversaries playbooks. They make it both easy to manage compromised devices during an engagement and often help aid in lateral movement.
Room Objectives
In this room, we will learn about Command and Control Frameworks in-depth to gain a better understanding of the following topics:
- How a Command and Control Framework operates
- The various components that you may use.
- How to set up a basic Command and Control Framework
- Use Armitage or Metasploit to gain familiarity with a Command and Control Framework
- How to administer a Command and Control Framework
- OPSEC Considerations while administering a Command and Control Framework
- And much more!
Command and Control Framework Structure
What is a Command and Control Framework
While trying to digest the various components of a C2 framework, it may be intimidating. However, they don’t have to be. In order to better understand what a C2 framework is at its most basic level, think of a Netcat listener (the C2 server) that is capable of handling many reverse shells calling back at once (C2 Agents). It’s a server but for reverse shells. Unlike Netcat, almost all C2 frameworks require a special payload generator. This is usually a feature that is built into the framework itself. For example, Metasploit is a C2 Framework that has its own payload generator, MSFVenom.
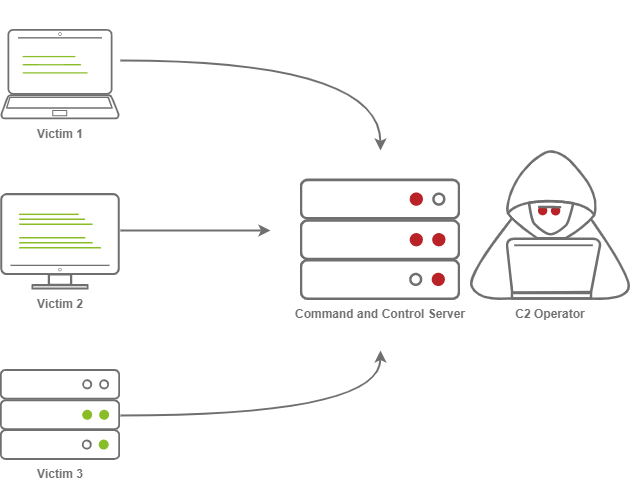
The Diagram above depicts three compromised clients calling back to a C2 Server.
So what exactly makes C2 frameworks better than a normal Netcat listener? It seems like all someone needs to do is implement session management into Netcat, and you have the same thing? While this is true, C2 frameworks shine in their “Post Exploitation” features.
Command and Control Structure
C2 Server
In order to understand a Command and Control framework, we must first start by understanding the various components of a C2 server. Let’s start with the most essential component - The C2 Server itself. The C2 Server serves as a hub for agents to call back to. Agents will periodically reach out to the C2 server and wait for the operator’s commands.
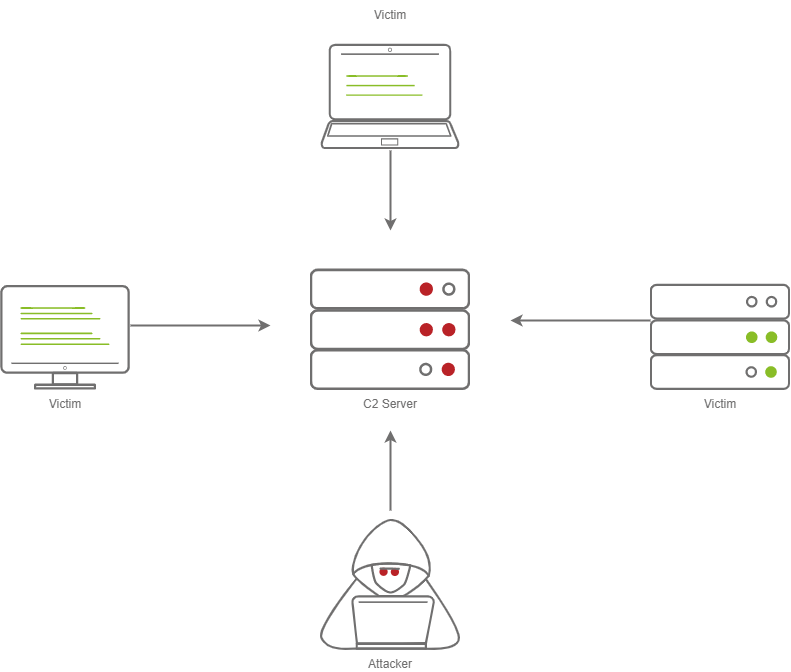
This screenshot depicts a basic C2 server diagram.
Agents / Payloads
An agent is a program generated by the C2 framework that calls back to a listener on a C2 server. Most of the time, this agent enables special functionality compared to a standard reverse shell. Most C2 Frameworks implement pseudo commands to make the C2 Operator’s life easier. Some examples of this may be a pseudo command to Download or Upload a file onto the system. It’s important to know that agents can be highly configurable, with adjustments on the timing of how often C2 Agents beacon out to a Listener on a C2 Server and much more.
Listeners On the most basic level, a listener is an application running on the C2 server that waits for a callback over a specific port or protocol. Some examples of this are DNS, HTTP, and or HTTPS.
Beacons A Beacon is the process of a C2 Agent calling back to the listener running on a C2 Server.